Amid the crowds of the cafe and the noise of urban life, I entered a quiet cafe. It was a coffee session that looked like a character that lacked comfort. As I relaxed, I had the thought of how safe my Wi-Fi connection was available at the venue.Dangers of Internet access to cafes and public places
This was not an unusual decision, as many tend to take advantage of public Wi-Fi networks. But unless I realize then, this rug I chose for my break could open doors to an unknown world. At this moment, a surprise journey began in the world of digital security, where curiosity turned out to be unsafe.
In this article we will talk about hidden tools such as Wireshark, Nmap and Ettercap, and how they can turn quiet communication moments into a safety impasse.Dangers of Internet access to cafes and public places
What’s the risk of unprotected network connectivity?

In public cafes and markets, many use Wi-Fi networks without thinking about how safe this connection is. Unfortunately, there is a great risk in this habit of connecting to unprotected networks, so what is the risk?
Sometimes many of us lack awareness that connecting to an unprotected network makes us vulnerable to hacking and stealing personal information. Once connected, a potential hacker can monitor all your online activity, whether it’s logging into your accounts or browsing websites. Some wonder: How can a hacker track my activity around the unprotected network?
The answer lies in the simplicity of things, where those interested in hacking have sufficient means to spy and follow up on users’ activity through these networks. Specifically, hackers use sophisticated tools to access your personal information. Among these lethal tools we find Wireshark, Nmap and Ettercap, tools used to screen and analyze data traffic across the network.
Wireshark, for example, allows monitoring of data sent from your device to the Internet. A program such as Nmap scans networks to detect connected devices and active services. While programs like Ettercap can do Man-in-the-Middle attacks to grab traffic data and sensitive information.
Prevention is better than cure, so users must be careful and take the necessary security measures when communicating with public networks.
How can a hacker track my activity around the unprotected network?
When you connect to unprotected WiFi, hackers open the door to monitor your activities and steal your personal information. How can they achieve this? Here we will take a look at tools such as Wireshark, Nmap and Ettercap that are used by those interested in hacking to analyze data traffic and spying on the network.
The most popular tracking and spying tools on information sent via the network
- Wireshark

- Open source tool that allows me to eavesdrop on the web
- Wireshark, an open source tool used to analyze network data traffic. Wireshark is one of the most popular network analysis and monitoring tools, providing an easy-to-use graphical interface to check and understand data traffic between connected devices.
- Wireshark has constantly evolved to meet the needs of professionals in the field of computer networks and information security, and specialists use it to diagnose problems and analyze network security.
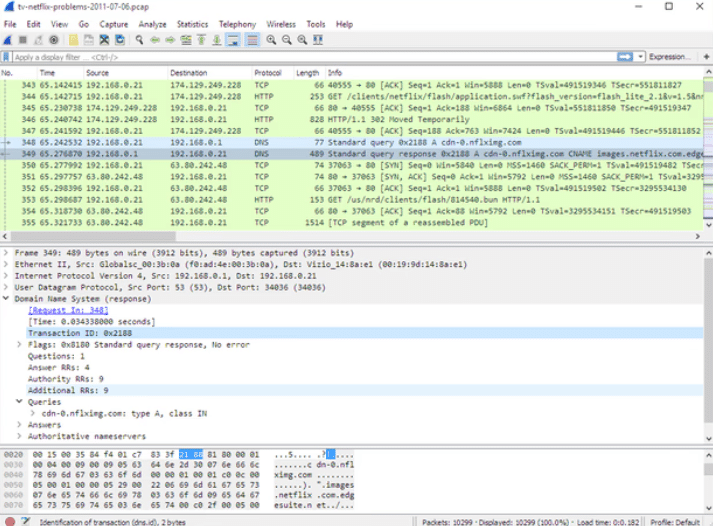
- When trying to access any app or website even if it is protected, just put any user & pass personal information you will easily show me the hacker with device type, ip address and browser type
- 2Nmap
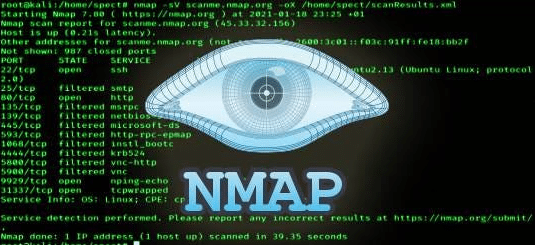
- This tool allows network hedging to also allow all connectors to see the network and the IP address and you can see the open ports and allow me to hack into devices and sites and detect gaps such as the ejection of connectors and is available on all operating systems.
- ettercap

- These are some of the most dangerous network penetration tools and are the hacker’s favorite enables him to intercept the network connection and collect and hack the password, which characterizes the tool as simple, not complex, and allows me to carry out the evil twin attack
You might like :
- Impact of artificial intelligence on creative writing
- engagement invitation message
- baby shower invitation message
- baby girl first birthday invitation message
- lunch invitation message
Some of the tools that help hack the wi-fi into the Kalilinux system
- Aircrack-ng
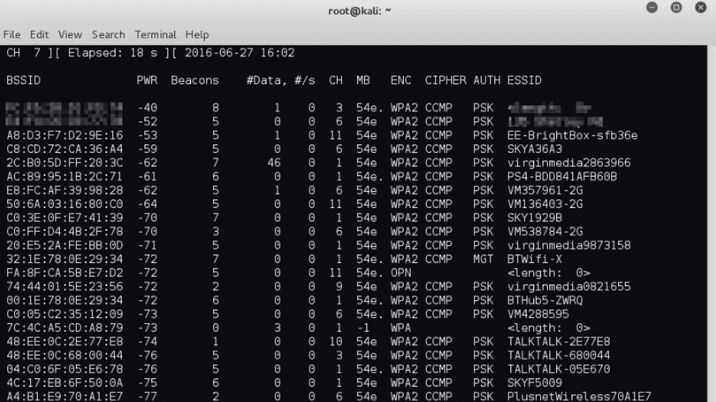
Aircrack-ng is a powerful tool used to penetrate WiFi networks protected by WEP or WPA/WPA2 encryption. Aircrack-ng is a set of tools that allow the user to analyze data traffic and infer used Wi-Fi keys. Enables them to be used to test and improve the safety of wireless networks.
- Reaver

Reaver is a tool mainly used in WPS-protected Wi-Fi Protected Setup hack attacks. Reaver carries out the Brute Force attack to extract the network’s PIN information and then use it to access the wireless key.
- Pixiewps
Pixiewps is a tool used to exploit gaps in the WPS system, and carries out angle-based attacks (Pixie Dust Attack). Used for identity verification information and wireless keys for targeted WiFi networks.
- Wifite
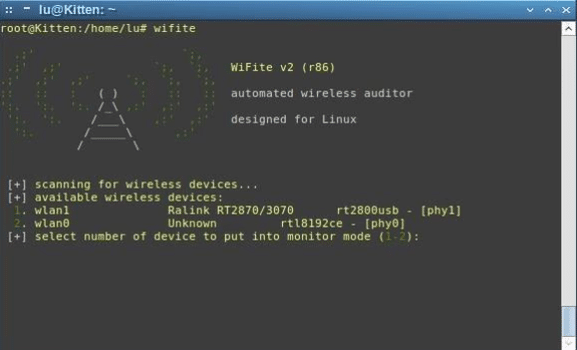
Wifite is a tool used to facilitate and speed up WiFi hacks. Wifite scans ambient networks and implements automatic attacks using a variety of tools such as Aircrack-ng and Reaver. Used to improve the efficiency of penetrations.
- Fern Wifi Cracker
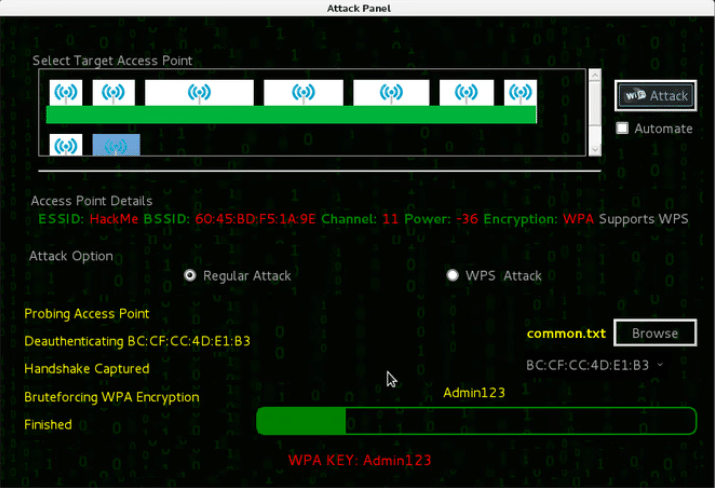
Fern Wifi Cracker is one of the leading tools in hacking Wi-Fi networks. Fern provides an easy-to-use graphic interface and supports a wide range of attacks and technologies. Users can use Fern to explore networks, identify vulnerabilities, and implement attacks to access Wi-Fi keys.
Before finishing, I hope that these tools will not be used to harm others. I would also like to understand the dangers of connecting to unprotected networks to preserve personal information and to keep me safe.

